Using technology to overcome POS maintenance challenges.
By Andy Zysk
Restaurants are a huge cybercriminal target. Attacks to restaurants are among the most publicized of breaches. All it takes is one record or credit card being compromised at a single location and the brand suffers bad press. It takes years for customers to regain their trust in the restaurant’s ability to protect their data. For smaller operators, the costs associated with the breach can be too great and force the doors to close.
For any single restaurant, there are many devices to protect: POS systems, tablets, kitchen video systems, PCs, laptops and kiosks. The larger the brand, the greater the need for automation. If a device is being used as part of the POS, it needs to be protected.
Here are some common concerns and ways to use technology to overcome POS maintenance challenges.
Security
Restaurants have critical security needs. Although credit card information will always come to mind first, the information that surrounds that card number is much more valuable to the cybercriminal. Some of the information behind that card number is valuable enough to begin laying the groundwork for identity theft — a fraud much more difficult to recover from for the individual.
Remote monitoring and management (RMM) software can be used to ensure that all aspects of the network devices and applications are protected. Keep in mind, software can only do so much. The staff still needs to be vigilant and follow security procedures, such as strong passwords, avoiding malware links, and how to spot, shut down and report attacks.
PCI-DSS
If the restaurant deals with credit cards, you must abide by PCI-DSS rules. Although the POS software itself has gone through rigorous testing to obtain compliance, restaurants also need to understand their responsibilities for protecting their most valued resources: their customers. There are six main categories of regulations. (See chart.)
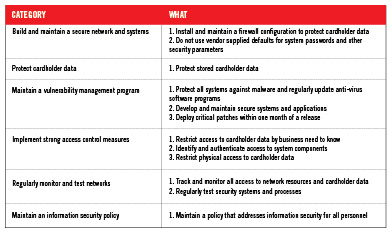 RMM software can help restaurants with many of these compliancy activities. Without proper controls, many restaurants are likely vulnerable. Operating systems patch management can be set to automatically apply patches, but when critical patches are released, many have no insight into whether those patches were applied or not. Often these concerns are called into the support centers to investigate and resolve. The process of connecting to individual devices and verifying current patch revision is time consuming and inconvenient — if possible at all. It is common practice to set up automatic updates, but with no visibility into the devices, it may be impossible to tell if those critical updates have been applied. With RMM and patch management implemented, the restaurant can be assured that all critical patches have been applied to all appropriate end points.
RMM software can help restaurants with many of these compliancy activities. Without proper controls, many restaurants are likely vulnerable. Operating systems patch management can be set to automatically apply patches, but when critical patches are released, many have no insight into whether those patches were applied or not. Often these concerns are called into the support centers to investigate and resolve. The process of connecting to individual devices and verifying current patch revision is time consuming and inconvenient — if possible at all. It is common practice to set up automatic updates, but with no visibility into the devices, it may be impossible to tell if those critical updates have been applied. With RMM and patch management implemented, the restaurant can be assured that all critical patches have been applied to all appropriate end points.
Unmanaged Antivirus/Anti-Malware
POS systems are targets for remote attacks, which can include:
- Use of stolen credentials.
- RAM scraping (attackers access data meant to be encrypted while it is in RAM in plain text).
- Keylogging malware.
- Sprees (single actor with many victims).
- And all manner of automated attacks.
The common thread in the most successful, large-scale attacks remains malware. The cybercriminal is often only after credit card and related personal information. As attacks become more sophisticated, older techniques are still just as effective when the restaurant is not protected. One such approach is what Verizon calls ‘smash and grab:’
- POS server is visible on the network.
- POS has a default login.
- Hacker leverages the gap to install malware.
- Malware grabs the payment card data as it’s being processed.
RMM software can assist with ensuring the restaurant antivirus/anti-malware applications are kept up to date at all times and critical patches are applied when required.
Reactive vs. Proactive Issue Resolution
Even in a single restaurant, there are many devices that need to be protected, monitored and fixed. The restaurant staff can visually tell that a device is “misbehaving,” but the solution may not be easily diagnosed with basic troubleshooting. Rebooting devices can clear issues in the short term, but without proper diagnostics, the issue is bound to return. With large-scale installations, the POS systems are widely distributed — only adding to the difficult tasks of remote troubleshooting.
Many organizations are saddled with site visits and/or remote connection/troubleshooting, so that they can maintain, update and fix devices. In most cases, calls are being made when devices have already failed. Technicians are called to sites to replace already failed devices or to diagnose these units that are slowly losing life. In the long run, this is an untenable solution.
RMM software automates all these functions and eliminates many of the site visits. Using RMM software, administrators can establish performance thresholds. When these are exceeded, technicians receive alerts so that they can take action. Issues can be fixed before they become a problem, and before the end user notices a thing. All patch management and updates can be tested centrally and then pushed out to all machines or select groups, once they are proven safe.
An example of how this information has been used to prevent a hardware failure happened while monitoring CPU temperature readings. Throughout normal monitoring, an alert was generated because the CPU temperature was rising above an acceptable threshold. This alert was sent to a support team who discovered that the root cause of the temperature spike was a third-party application loaded by the customer that began “misbehaving.” This application was causing the CPU to constantly run at 80% to 90% capacity, which caused the CPU to heat up. The support team disabled the application from running, enabling the CPU temperature to resume a normal operating range.
Remote Monitoring & Management Software
RMM is a system and endpoint management solution for IT teams. In the case of the POS systems, RMM can increase device uptime, performance and security, and allow teams instant access into all devices within the system. With an RMM solution configured, the staff can automate a great deal of common tasks that would otherwise take hours/days to complete:
- Discover, audit, inventory and monitor clients, servers and the network.
- Perform patch management.
- Monitor devices for performance or problems.
- Resolve issues — including non-working hard drives.
- Maintain and run antivirus/anti-malware tools.
- Real-time reports to support PCI audits.
— Andy Zysk is manager of the managed services department for PAR Technology’s customer success organization. With over 20 years of experience in the POS technology industry, Zysk has been a developer of key support strategies for PAR’s POS software platforms. He is also head of PAR’s menu maintenance team.
